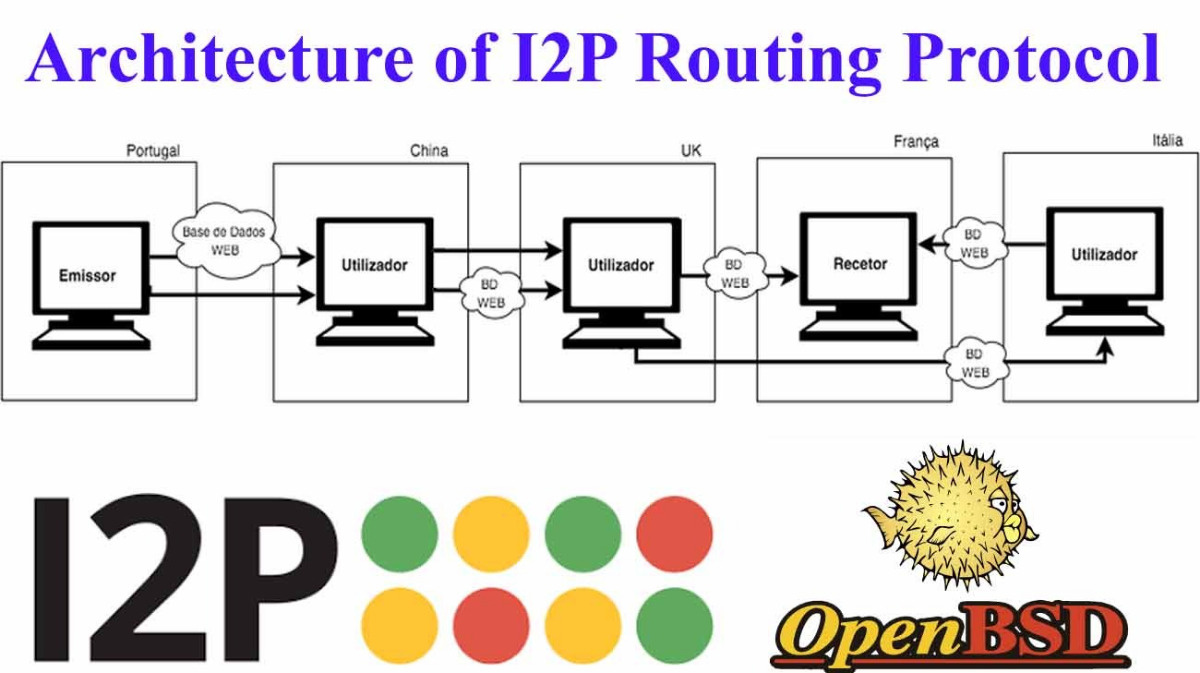
Link on Github --> https://github.com/Nieuport/news-and-links/blob/gh-pages/docs/2026.02.02.md
PatchGuard Peekaboo: Hiding Processes on Systems with PatchGuard in 2026 - https://www.outflank.nl/blog/2026/01/07/patchguard-peekaboo-hiding-processes-on-systems-with-patchguard-in-2026/
Breaking the Sound Barrier, Part II: Exploiting CVE-2024-54529 - https://projectzero.google/2026/01/sound-barrier-2.html
anyPDF decompilation - a highly evasive, fully undetected, signed PDF editor bundled with AdClicker Trojan and Spyware - https://rifteyy.org/report/anypdf-malware-analysis
Don't judge an audiobook by its cover: taking over your Amazon account with a Kindle - https://blog.thalium.re/posts/dont-judge-an-audiobook-by-its-cover-taking-over-your-amazon-account-with-a-kindle/
Introducing RelayKing – Relay To Royalty - https://www.depthsecurity.com/blog/introducing-relayking-relay-to-royalty/
#informatyka